作者:刘安
爱可生测试团队成员,主要负责 DTLE 开源项目相关测试任务,擅长 Python 自动化测试开发。
本文来源:原创投稿
*爱可生开源社区出品,原创内容未经授权不得随意使用,转载请联系小编并注明来源。
如何开启DTLE的HTTPS访问模式
DTLE默认提供的是HTTP的访问模式,但是在使用DTLE的过程中不免要通过API提交诸如数据库的用户名、密码、IP、端口等信息。如果这些信息被第三方获取到,那么对于数据库的使用者简直就是一场灾难。因此DTLE提供了HTTPS的访问模式,保护我们的信息安全。
启用DLTE的HTTPS访问模式需要SSL证书,如果你搭建的集群需要向外提供可信的服务可以向证书管理机构申请。本文使用自己生成的SSL证书来演示如何配置DTLE使HTTPS访问模式生效。
1. 下载安装DTLE
这里使用的是dtle-ce-4.22.01.0版本,注意先不要启动DTLE服务
shell> curl -O "https://github.com/actiontech/dtle/releases/download/v4.22.01.0/dtle-ce-4.22.01.0.x86_64.rpm"
shell> rpm -ivh dtle-ce-4.22.01.0.x86_64.rpm --prefix=/opt/dtle
2. 生成证书文件和私钥文件
# 需要安装openssl
shell> yum install openssl -y
shell> cd /opt/dtle/etc/dtle/
# 生成私钥文件
shell> openssl genrsa -out server.key 1024
Generating RSA private key, 1024 bit long modulus
....++++++
........++++++
e is 65537 (0x10001)
# 生成证书请求文件,此步骤可以全部回车,不输入任何信息
shell> openssl req -new -key server.key -out server.csr
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:Shanghai
Locality Name (eg, city) [Default City]:Xuhui
Organization Name (eg, company) [Default Company Ltd]:actiontech
Organizational Unit Name (eg, section) []:qa
Common Name (eg, your name or your server's hostname) []:dtle
Email Address []:852990221@qq.com
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
# 生成证书文件
shell> openssl x509 -req -in server.csr -out server.crt -signkey server.key -days 365
Signature ok
subject=/C=CN/ST=Shanghai/L=Xuhui/O=actiontech/OU=qa/CN=dtle/emailAddress=852990221@qq.com
Getting Private key
shell> ls
consul.hcl nomad.hcl server.crt server.csr server.key
3. 编辑nomad.hcl,配置证书文件和私钥文件
shell> vi nomad.hcl
...
cert_file_path = "/opt/dtle/etc/dtle/server.crt"
key_file_path = "/opt/dtle/etc/dtle/server.key"
...
4. 启动DTLE
shell> systemctl start dtle-consul dtle-nomad
5. 验证https开启成功
# 使用http访问
shell> curl -X POST "http://127.0.0.1:8190/v2/loginWithoutVerifyCode" -H "accept: application/json" -H "Content-Type: application/json" -d "{ \"password\": \"admin\", \"tenant\": \"platform\", \"username\": \"admin\"}"
Client sent an HTTP request to an HTTPS server.
# 使用https访问,但我们的证书没有通过CA认证
shell> curl -X POST "https://127.0.0.1:8190/v2/loginWithoutVerifyCode" -H "accept: application/json" -H "Content-Type: application/json" -d "{ \"password\": \"admin\", \"tenant\": \"platform\", \"username\": \"admin\"}"
curl: (60) Peer's certificate issuer has been marked as not trusted by the user.
More details here: http://curl.haxx.se/docs/sslcerts.html
curl performs SSL certificate verification by default, using a "bundle"
of Certificate Authority (CA) public keys (CA certs). If the default
bundle file isn't adequate, you can specify an alternate file
using the --cacert option.
If this HTTPS server uses a certificate signed by a CA represented in
the bundle, the certificate verification probably failed due to a
problem with the certificate (it might be expired, or the name might
not match the domain name in the URL).
If you'd like to turn off curl's verification of the certificate, use
the -k (or --insecure) option.
# 使用https访问,增加-k参数跳过检查服务器的SSL证书是否正确
shell> curl -s -k -X POST "https://127.0.0.1:8190/v2/loginWithoutVerifyCode" -H "accept: application/json" -H "Content-Type: application/json" -d "{ \"password\": \"admin\", \"tenant\": \"platform\", \"username\": \"admin\"}" | jq
{
"message": "ok",
"data": {
"token": "eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJleHAiOjE2NTAxMjAzNjcsImdyb3VwIjoicGxhdGZvcm0iLCJuYW1lIjoiYWRtaW4ifQ.I1XDK7Ar1JLKLWlxWEHX0vCWG07dDqBHieCBmjEVz0E"
}
}
shell> curl -s -k -X GET "https://127.0.0.1:8190/v2/nodes" -H "accept: application/json" -H "Authorization: eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJleHAiOjE2NTAxMjA0MjYsImdyb3VwIjoicGxhdGZvcm0iLCJuYW1lIjoiYWRtaW4ifQ.PoPwOWQF09uaUf6vu0rTPQVpLfF59UIhq-lLBBVhTbc" | jq
{
"nodes": [
{
"node_address": "127.0.0.1",
"node_name": "nomad0",
"node_id": "21bd1636-0beb-e4c6-34fd-d35be32414e9",
"node_status": "ready",
"node_status_description": "",
"datacenter": "dc1",
"nomad_version": "1.1.2",
"dtle_version": "4.22.01.0-4.22.01.x-952bb3d",
"leader": true,
"member": true
}
],
"message": "ok"
}
6. 抓包查看传输的信息
-
使用 https, 登录DTLE提交的信息是经过加密的:
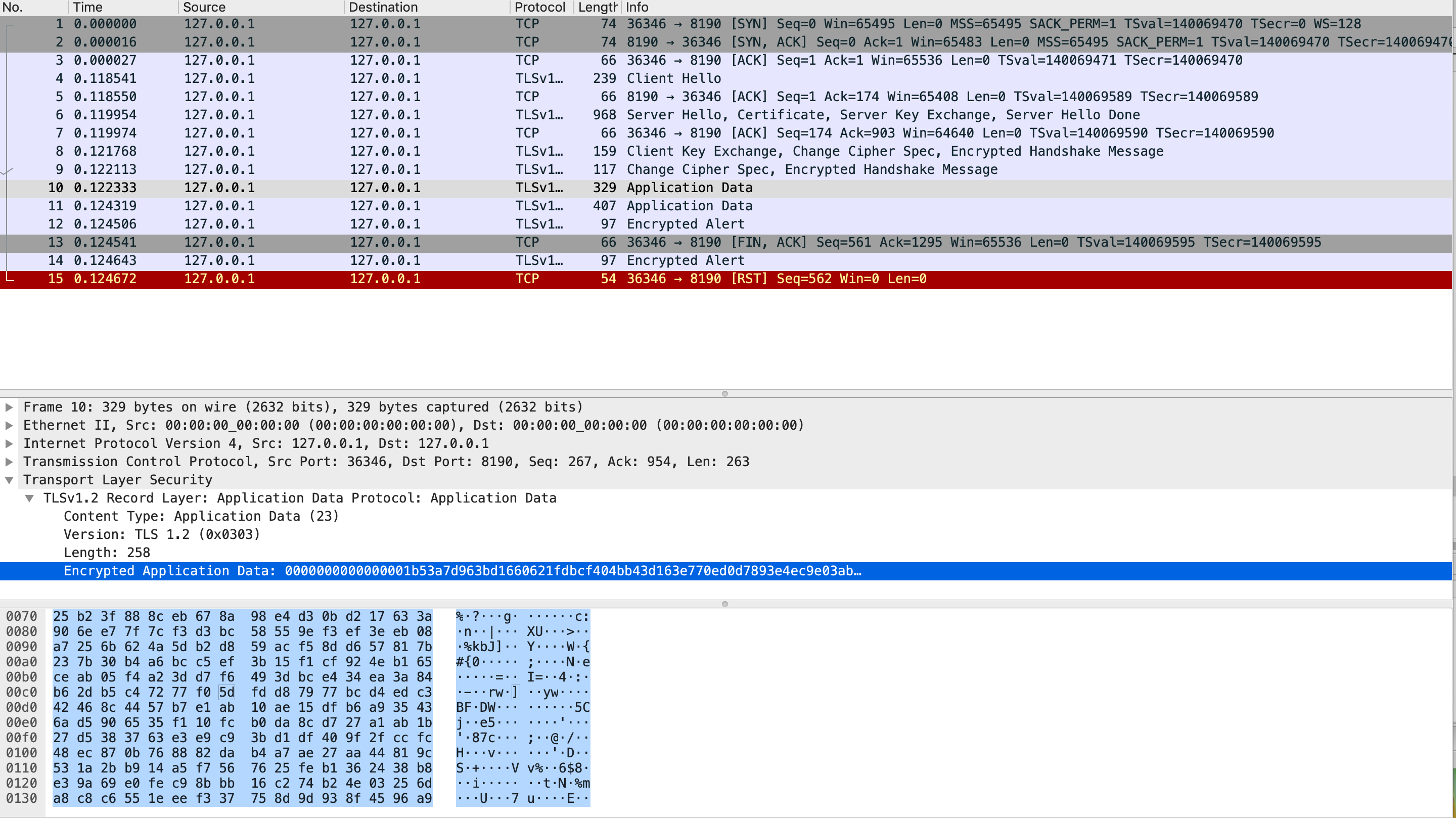
-
使用 http, 登录DTLE提交的信息是明文:
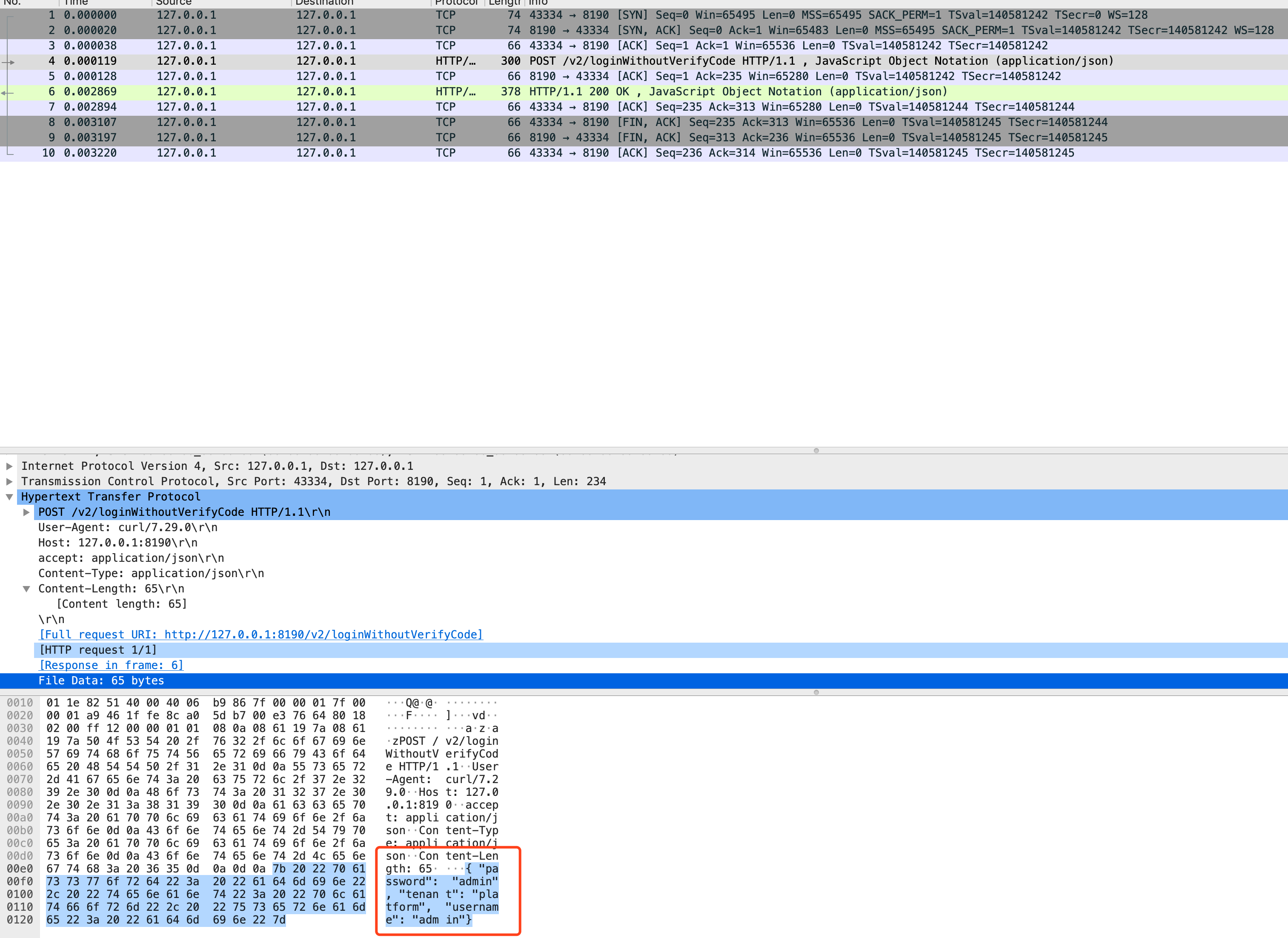
结论:
如果您在项目上使用DTLE来传输数据,请务必开启HTTPS访问模式来保护您的信息安全。